If there’s one thing working cross-functionally has taught me, it’s that secure access isn’t just a security priority; it’s a growth enabler. Slow logins and brittle VPNs kill momentum; over-permissive access invites incidents.
The difference often comes down to the platform behind the scenes. The strongest zero trust networking software don’t just gate access, they align identity, device posture, and app context so users get where they need to go, quickly and safely.
To see what truly stands out, I compared leading ZTNA solutions across policy depth, IdP/EDR integrations, deployment speed, and day-two operations.
If you’re searching for the best zero trust networking software for 2025, here are my top picks. Whether you’re standardizing on a single client or segmenting sensitive apps first, these platforms stood out for flexibility, scalability, and real-world usability.
5 best zero trust networking software for 2025: My top picks
- Palo Alto Networks IoT/OT Security: Best for enterprise IoT/OT visibility and control
For auto-discovering connected devices, assessing risk by behavior, and enforcing segmentation to block lateral movement. - Okta: Best for identity-driven access across mixed stacks
For secure SSO/MFA, fine-grained conditional access, and seamless integration with cloud and on-prem apps. - Zscaler Private Access: Best for zero-trust access to internal apps (no VPN)
For brokered user-to-app connectivity, continuous identity/device checks, and fast global access from anywhere. - ThreatLocker: Best for endpoint least-privilege and allowlisting
For default-deny application control, granular elevation approvals, and ransomware-resilient endpoint policies. - Cato SASE Cloud: Best for unified network + security at global scale
For converging SD-WAN and SSE, enforcing zero-trust policies from the cloud, and delivering consistent performance worldwide.
These best zero trust networking software are top-rated in their category, according to the latest G2 Grid Reports. Contact the sales team for accurate pricing details.
5 best zero trust network security tools I recommend
Zero trust networking platforms enforce “never trust, always verify” for application access across hybrid and remote work. Instead of routing users through network-level VPNs, they continuously validate identity, device posture, and context, then grant precise, app-level access that limits lateral movement.
The business case is straightforward: breaches are costly and common. IBM states the global average cost of a data breach is about $4.4 million, reflecting a 9% drop from the previous year, a decline largely attributed to organizations detecting and containing incidents more quickly..
With that in mind, I prioritized platforms that pair clean policy models and strong integrations (IdP/EDR/MDM) with reliable clients and clear visibility. Based on reviews, demos, and hands-on tests, these are the five I’d pick if you’re serious about operationalizing zero trust.
How did I find and evaluate the best zero trust networking tools?
I started with G2’s Grid Report, which ranks tools based on real user reviews and market presence, to move past surface-level comparisons. The Grid gave me a solid foundation that highlighted both established leaders and innovative challengers in the zero trust networking category.
I then used AI-assisted analysis to dig into hundreds of verified G2 reviews. I paid close attention to patterns around policy reliability and enforcement, ease of integration with identity providers (IdPs), EDR/MDM, and SIEM tools, depth of device posture checks and app discovery, and scalability across users, apps, and locations. This helped me see what security, IT, and networking teams actually value most — and where zero trust platforms sometimes fall short.
To bring the data into real-world context, I also connected with fellow G2’ers who work with zero trust access in security operations, IT, and network engineering. Their experiences validated the themes I found in the reviews and shed light on implementation speed, setup experience, and the day-to-day impact these platforms have on both user productivity and overall security posture.
All product screenshots featured in this article come from official vendor G2 pages and publicly available materials.
What makes zero trust networking software worth it: My opinion
I considered the following factors when evaluating the best zero trust networking software.
- Policy accuracy and enforcement: The best platforms go beyond broad network rules, enforcing least-privilege at the app level with continuous checks on user, device, and context — and handling complex scenarios without breaking workflows.
- Coverage across private apps and SaaS: Strong platforms secure east–west and user-to-app traffic alike, supporting legacy/private apps, modern SaaS, and even contractor/BYOD access with consistent controls.
- Identity, device, and security stack integrations: I prioritized tools that plug cleanly into IdPs, EDR/MDM, SIEM, and DNS/secure web gateways to keep policies and telemetry unified. Especially important for enterprise buyers, I considered platforms that support strong encryption, data residency options, and attestations like SOC 2/ISO 27001 to protect sensitive data.
- Segmentation and lateral-movement defense: Solutions that can discover apps, visualize flows, and enforce microsegmentation stand out for containing incidents and reducing blast radius.
- Scalability and flexibility: The best tools serve lean IT teams and large enterprises, offering sensible defaults, API/extensibility for advanced use cases, and a global footprint that holds up under load.
The list below contains genuine user reviews from the Zero Trust Networking category. To be included in this category, a solution must:
- Utilize adaptive authentication to continuously verify user permissions
- Allow for network segmentation to simplify and broaden policy enforcement
- Monitor traffic and user behavior for future inspection and analysis
*This data was pulled from G2 in 2025. Some reviews may have been edited for clarity.
1. Palo Alto Networks IoT/OT Security: Best for enterprise IoT/OT visibility and control
Among platforms built to secure mixed IT/OT environments, Palo Alto Networks IoT/OT Security repeatedly shows up in G2 reviews for doing the unglamorous work well: discovering and classifying devices, surfacing behavioral anomalies, and giving teams a unified, searchable view of what’s actually connected.
If your goal is to move from guesswork to a defensible, real-time asset picture, this is the kind of foundation you need.
What stood out in my evaluation (and echoed by G2 users) is the unified IT/OT lens. Reviewers consistently highlight how the product brings operational technology into the same line of sight as traditional IT, making it easier to see PLCs, HMIs, cameras, sensors, printers, without stitching together multiple tools. That consolidated view isn’t just cosmetic; G2 users say it shortens triage because ownership is clearer and suspicious behavior is easier to spot in context.
Discovery and classification accuracy also came through strongly in G2 reviews. Reliable fingerprinting of IoT/OT assets and faster inventory buildouts translate to fewer blind spots, quicker identification of unknowns, and more confidence when you attach policy. Paired with behavioral and anomaly detection, teams report actionable alerts that improve with tuning — less noise, more signal — so responders aren’t sifting through endless low-value events.
Integration depth is another repeated theme in G2 feedback. The product plays well with identity (IdP), endpoint (EDR/MDM), SIEM, ticketing, and NGFW/Prisma workflows. That matters when you want detection to lead to enforcement or when you need incidents to show up where your team already lives; reviewers frequently mention how these connections reduce swivel-chairing, tighten response loops, and make audit narratives clearer.
G2 users also call out dashboards and reporting. Topology views, risk summaries, and device-level drill-downs make complex environments legible and defensible: you can show what’s talking to what, why it’s risky, and what actions you took. For many teams, that “show your work” moment is what turns a good pilot into an operational win.
G2 reviewers like the depth and unified view, but several note the console can feel dense at first, especially in multi-site rollouts where roles, groups, and workflows need planning. That said, the same G2 feedback points to a quick settlement once onboarding is done: alert noise drops, ownership is clearer, and investigations move faster as OT signals feed existing SIEM/SOAR pipelines.
Because it consolidates meaningful capabilities, some G2 users describe pricing and licensing as being on the higher side and say they’d like clearer guardrails as device counts grow. However, teams that plan for future scale and forecast usage early on report that costs become easier to predict and that consolidation ultimately offsets spend by reducing support tickets, closing visibility gaps, and strengthening audit readiness.
Overall, rated a 4.3/5 on G2, reviewers appreciate that it can introduce it alongside existing network and security architectures and then elevate controls as visibility improves. It’s a practical path to reducing risk without pausing the business. Repeated G2 themes point to a platform that delivers a trustworthy inventory, fewer blind spots, and faster, better-informed decisions when something starts behaving out of band.
What I like about Palo Alto Networks IoT/OT Security:
- The unified IT/OT lens makes inventories and investigations feel sane. I can see PLCs, HMIs, cameras, and endpoints in one place, which lines up with what G2 users repeatedly call out about faster, clearer triage.
- Discovery/classification plus meaningful anomaly detection gives me actionable alerts; signal improves with tuning, and integrations (IdP/EDR/SIEM/NGFW) push those insights into the tools my team already uses.
What G2 users like about Palo Alto Networks IoT/OT Security:
“We utilize Palo Alto Networks OT Security (GlobalProtect) to allow us to work remotely. This was especially required during the COVID-19 pandemic. In addition, it allowed us to work at various locations around the earth, since there were multiple gateways. I like how there were multiple ways to sign into Palo Alto Networks’ Global Protect. For example, we were able to sign in via Global Protect via (Employee Key Card, password/username, MFA hardware). This is easy to utilize everyday, since Employees need to sign into our enterprise network in order to access Company documents, code, etc. We basically needed this every day while working remotely.”
– Palo Alto Networks IoT/OT Security review, Verified User in Defense & Space.
What I dislike about Palo Alto Networks IoT/OT Security:
- The console favors depth and control, which suits teams that want granular policy and rich telemetry, but it can feel dense at first for groups expecting a plug-and-play setup.
- Enterprise-grade coverage and integrations scale well, though pricing/licensing can require upfront modeling as environments grow. Teams seeking simple per-device predictability may want clearer cost guardrails.
What G2 users dislike about Palo Alto Networks IoT/OT Security:
“I wish the licensing were more straightforward—every extra sensor seems to nudge the bill up. The UI slows down when I pull a month of logs, and a few OT-specific signatures still fire noisy alerts that we have to tune out. Reporting exports are limited to CSV, so building Grafana dashboards means extra ETL work on our side.”
– Palo Alto Networks IoT/OT Security review, Ramon F.
Explore the best Network Access Control software on G2. Compare top NAC tools built to enforce zero trust policies and secure every device on your network.
2. Okta: Best for identity-driven access across mixed stacks
Among identity platforms powering zero trust access, Okta shows up repeatedly in G2 reviews for making day-to-day sign-in simpler while tightening control behind the scenes. It’s built for teams that want clean SSO, dependable MFA, and broad app integrations without forcing users through a maze of one-off credentials.
If your goal is to centralize identity and make access decisions based on user, device, and context, across cloud and on-prem, this is a strong anchor.
It delivers on core outcomes G2 users care about: friction-light single sign-on that cuts password sprawl; reliable authentication (from OTP and push to phishing-resistant methods) that doesn’t bog down everyday workflows; and deep integrations with a wide ecosystem of SaaS and legacy apps so you’re not building brittle, one-off connectors. In fact, 93% of G2 users rate the authentication experience highly.
Reviewers consistently highlight how quickly users adapt to the Okta dashboard/portal, launching the apps they need without hunting links, and how admins can plug Okta into the rest of the stack (HRIS for automatic onboarding/offboarding, EDR/MDM for device posture, SIEM/ticketing for visibility and handoffs). That ecosystem fit shows up in the feedback as fewer “where do I log in?” tickets and smoother day-two operations.
From an operator lens, G2 reviewers repeatedly call out usability. The setup feels straightforward, policies are understandable, and everyday management doesn’t require deep identity engineering. 94% of G2 users rate its self-service password reset feature highly.
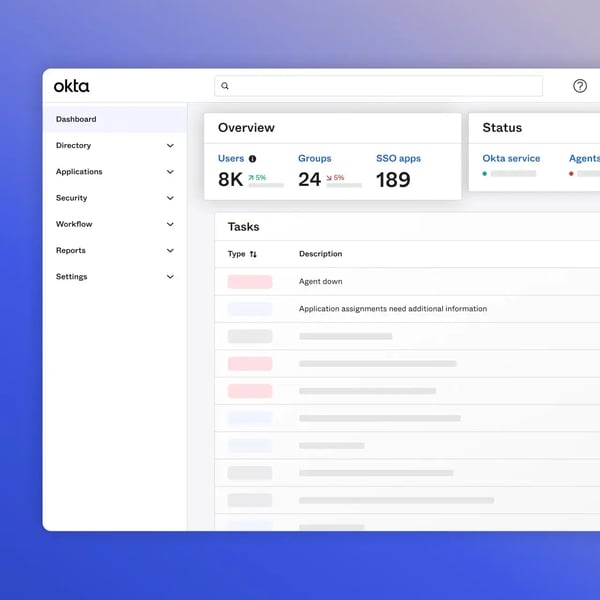
Teams like that app assignment and group-based policies scale cleanly as the org grows, and that availability/performance is solid enough that sign-in fades into the background for most users. When the platform is wired into your existing tools, audits get easier because access paths are centralized and logged.
Security depth beyond SSO. Reviewers frequently highlight Okta’s strong policy engine and adaptive access controls, including context-aware decisions based on device, network, and risk signals, which strengthen zero trust posture without adding complexity. Extensive integration ecosystem. Multiple reviews praise Okta’s wide connector library and prebuilt app integrations, which reduce custom development work and make it easier to plug identity into the broader security stack.
Users also say that Okta is reliable and highly available. Several users point to consistent uptime and strong performance, noting that authentication remains stable even as traffic scales or during peak usage periods.
Let’s talk about console density. G2 reviewers value the control and breadth, fine-grained policy and broad integrations, while noting the console can feel busy if you’re expecting plug-and-play. That density suits admins who prioritize high-signal telemetry and precise policy design; teams seeking a lightweight, minimalist UI may find it more than they need.
G2 reviewers also talk about stricter access posture. Strong policies and device checks raise assurance on sensitive access, and G2 users note this can surface more prompts than “invisible” setups. That’s a win for organizations that favor risk-tight enforcement; if your bar is minimal interruption above all else, this level of scrutiny may feel heavier.
The repeated G2 themes and a strong 4.5/5 rating on G2 point to Okta as a dependable identity core for zero trust: easy SSO, strong MFA, and broad integrations that make secure access feel routine. If you invest a bit of time in console orientation and tune MFA/session policies to match your risk model, you get the payoff most reviewers describe — fewer credentials to manage, clearer access paths, and a cleaner handoff between security and productivity.
What I like about Okta:
- Friction-light SSO with a familiar app portal that users adopt quickly. G2 reviewers repeatedly credit this with fewer “where do I log in?” tickets and smoother day-to-day access.
- It has a broad ecosystem fit: deep integrations with SaaS/legacy apps plus HRIS, EDR/MDM, SIEM, and ticketing, so onboarding/offboarding and incident handoffs feel predictable.
What G2 users like about Okta:
“What I like best about Okta is how effortlessly it brings everything together. Instead of juggling multiple logins and passwords, I just sign in once and boom, I’m in. Whether its work apps, email, or tools I use daily, Okta makes access feel seamless and secure. The peace of mind knowing that multi-factor authentication is quietly working in the background is a huge plus. Its like having a smart gatekeeper who never sleeps. Also, the interface is clean and intuitive — even for someone who’s not super tech-savvy. It just works, and that’s what I appreciate most. The integration is very easy as well.“
– Okta review, Mohammed O.
What I dislike about Okta:
- The console prioritizes breadth and granular control, which power users will appreciate, but it can feel busy at first until roles, groups, and workflows are dialed in.
- Stronger MFA and device checks raise security posture, though some teams may notice extra prompts until risk-based rules and session policies are tuned to their environment.
What G2 users dislike about Okta:
“The main drawback is that the initial setup and configuration can be a bit complex, especially for teams without much experience in identity management. Also, the pricing can feel a little high for smaller companies. However, once it is properly set up, the platform works very reliably.”
– Okta review, Daniel Alberto J.
3. Zscaler Private Access: Best for zero-trust access to internal apps (no VPN)
Among zero trust options for private app access, Zscaler Private Access (ZPA) shows up repeatedly in G2 reviews for doing what most teams actually need: broker fast, policy-driven, user-to-app connectivity. If your goal is to retire brittle VPN tunnels, reduce lateral movement, and give users a consistent way to reach internal web, client-server, and cloud apps from anywhere, ZPA is built for that job.
What G2 users call out most often is how secure access feels routine once ZPA is in place. In fact, 92% of G2 users rate the application security highly. The combination of identity-aware policies and least-privilege access means you can tighten control while keeping the experience simple, people launch the apps they need, and nothing else.
Reviewers also highlight the global footprint and scaling behavior: standing up access for distributed teams and contractors is straightforward, and policies can expand with new apps and regions without major re-architecture. In day-to-day terms, that translates into fewer “can’t reach the app” tickets and less time spent micromanaging network paths.
The time-to-value and setup practicality often comes up as a positive in G2 reviews. Many admins describe the initial rollout as clear. There are publishing apps, mapping policies to identity groups, and onboarding users with minimal to no friction. ZPA’s ecosystem fit also gets consistent praise: integrations with major IdPs for SSO/MFA, plus hooks into EDR/MDM and SIEM/ticketing, help teams keep identity, device posture, and audit signals in one loop.
Let’s talk about performance. Users note snappy access and low perceived latency compared to legacy VPN, especially for web apps, with fewer slowdowns due to tunnel congestion. Coupled with client and connector architecture that abstracts away network complexity, many teams say ZPA makes remote access feel invisible: users click, the service verifies identity and device posture, and the session just works. For IT, that “feels like SaaS” quality is a big part of why ZPA replaces tactical VPNs rather than sitting next to them.
Several G2 reviewers say the agent/client needs hands-on tuning in the first couple of weeks (tightening rules, mapping app segments, refining device-posture checks). This is best for teams that want granular, policy-driven control rather than pure plug-and-play. After policies settle, VPN tickets drop, access is predictable and fast, and security has clear visibility into who accessed what, from which device, under which conditions.
G2 budget owners note that pricing scales with footprint (regions + app-dense estates), so you’ll need growth modeling up front. Suitable for organizations planning global coverage and broad integrations; less ideal if you expect flat, set-and-forget pricing. With early modeling, spend becomes predictable, consolidation offsets costs so teams see durable gains, less lateral movement, fewer brittle tunnels — and a user experience where people don’t fight.
A modest upfront investment in client/policy tuning and scale modeling yields what teams value most: fast, predictable private-app access, fewer VPN tickets, and clear end-to-end visibility. In practice, ZPA scales with your business and largely gets out of the way—tightening control without adding friction.
What I like about Zscaler Private Access:
- Secure access feels routine: identity-aware, least-privilege user-to-app connectivity and reducing “can’t reach the app” tickets.
- Strong ecosystem fit and rollout: clean IdP/SSO/MFA integration plus hooks into EDR/MDM and SIEM/ticketing; admins repeatedly note a clear, methodical initial setup and predictable day-two ops.
What G2 users like about Zscaler Private Access:
“What I like most about Zscaler Private Access is that it completely removes the hassle of using a traditional VPN. Once it’s set up, users can securely access internal apps from anywhere without worrying about connecting to the corporate network. The zero-trust approach feels much safer because access is given only to what’s needed. It also integrates nicely with identity providers like Okta or Azure AD, which makes user management simple. One more advantage is that it notices each and every Ethernet connection.”
– Zscaler Private Access review, Rushi P.
What I dislike about Zscaler Private Access:
- The client and policy model prioritize granular control and continuous checks, which is great for security posture, but the first weeks may involve tuning app segments and posture rules to minimize prompts.
- Enterprise-grade coverage and global scale are strengths, though pricing/licensing can benefit from upfront modeling as app inventories and regions expand, especially in large, app-dense environments.
What G2 users dislike about Zscaler Private Access:
“At times, the initial configuration and policy setup can be a bit complex, especially for new administrators. The troubleshooting process when users face access issues could also be more intuitive, as logs and diagnostics sometimes require deeper technical expertise. Additionally, occasional latency can occur when connecting to applications hosted in certain regions. However, once properly configured, it performs very reliably and requires minimal maintenance.”
– Zscaler Private Access review, Pratik K.
4. ThreatLocker: Best for endpoint least-privilege and allowlisting
Among endpoint controls built for a default-deny posture, ThreatLocker shows up repeatedly in G2 reviews for doing the blocking-and-tackling that actually shrinks the attack surface. These include application allowlisting/whitelisting, network and storage control, and guardrails that stop unknown executables before they run.
It’s a strong fit for security teams that want granular, policy-driven control on Windows/macOS/Linux endpoints—especially MSPs and lean IT groups that need to enforce least privilege without standing up a full EDR engineering function.
What stood out in my evaluation — and echoed across G2 reviews — is how quickly you can move from permissive to default-deny without paralyzing users. Reviewers repeatedly call out application control as the anchor: build a clean inventory of what’s allowed, then let ThreatLocker handle the rest. In practice, that means fewer “mystery binaries” and far less room for ransomware and script-based abuse. Paired with Ringfencing® to constrain what an allowed app can touch (e.g., which processes it can spawn, what it can read/write), teams describe a meaningful drop in risky behaviors without breaking legitimate workflows.
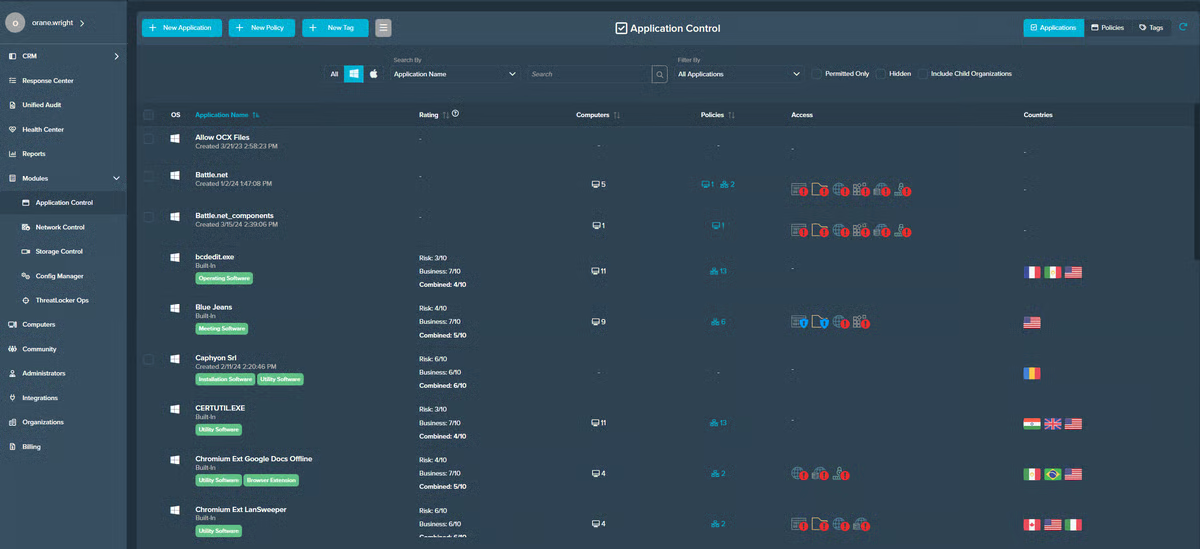
G2 users also highlight the breadth of policy controls beyond applications: Network Control to restrict outbound/inbound communications, and Storage Control to govern USB/external media use. That layered approach shows up in feedback as tangible outcomes — blocking lateral movement paths, preventing data exfil over unauthorized channels, and eliminating “USB roulette” without endless manual policing. The net effect is that everyday endpoint activity becomes predictable and explainable, which simplifies audits and incident timelines.
Another recurring theme is time-to-value. Many reviewers describe straightforward deployment and onboarding that get you to an enforceable posture quickly, with intuitive management once policies settle. The admin interface and policy views are frequently credited for making a complex control model legible—teams can see what was blocked, why, and what rule adjusted the outcome.
Just as importantly, G2 users consistently praise support: fast responses, hands-on guidance during rollout, and collaborative tuning when approvals spike or an edge case appears. That “help when you need it” loop is a big part of why ThreatLocker lands well with MSPs and resource-constrained IT teams.
G2 reviewers consistently call out the depth and precision the platform brings to access control, with many noting that the first few weeks are best spent refining approvals, fine-tuning policy groups, and aligning workflows, particularly in multi-site or mixed-OS environments. Because the agent and UI are designed for maximum control and visibility, teams expecting a purely plug-and-play experience often invest a little time in training and policy design up front. Once baselines are tuned, approvals normalize, and the platform largely fades into the background, reducing noise while delivering more predictable and secure access.
The default-deny posture is a deliberate design choice, and G2 feedback suggests it can surface more prompts early in a deployment. Teams that stage their rollout, communicate expectations clearly, and tighten Ringfencing®, Network, and Storage policies report that the signal stabilizes rapidly. As policies mature, approvals drop to a manageable rhythm, and users benefit from a secure, predictable experience, one that raises the security bar without creating new friction.
Overall, rated a high 4.8/5 on G2, ThreatLocker stands out for less noise, fewer blind spots, and far fewer “why did this run?” tickets.
What I like about ThreatLocker:
- Default-deny with allowlisting + Ringfencing makes endpoint behavior predictable. I can show exactly what ran, what it was allowed to touch, and why a block occurred.
- Layered Network/Storage Control closes common abuse paths (unauthorized outbound traffic, USB misuse) without endless manual policing, which G2 users say simplifies audits and day-to-day ops.
What G2 users like about ThreatLocker:
“ThreatLocker is a powerful security solution that gives administrators full control over what users can install, run, or script. Its default-deny approach ensures that only explicitly approved actions are allowed, making it easy to sleep at night knowing that even if users click on dangerous files, they won’t execute in secure mode.”
– ThreatLocker review, Graham T.
What I dislike about ThreatLocker:
- The console’s precision rewards teams that invest in early policy hygiene, expect a short phase of tuning approvals and refining groups before noise settles.
- If you want pure plug-and-play, plan a bit of enablement/training; most reviewers note value unlocks fastest when admins learn the workflow for edge-case approvals in multi-site or mixed-OS estates.
What G2 users dislike about ThreatLocker:
“ThreatLocker is a complex tool that offers many features with granular control. For that reason it does come with a large learning curve. It is highly recommended that you work closely with their support team until you are completely comfortable with the ins and outs of the software.”
– ThreatLocker review, Bryan S.
5. Cato SASE Cloud: Best for unified network + security at global scale
Among platforms built to converge networking and security in the cloud, Cato SASE Cloud shows up repeatedly in G2 reviews for making distributed connectivity feel simpler and more predictable. It’s designed for teams that want to collapse SD-WAN, secure web gateway, CASB, FWaaS, and ZTNA into a single service running on a global backbone, so users get consistent performance and security whether they’re in a branch, at home, or on the move.
If your goal is to replace a patchwork of appliances and point tools with one policy plane and one client, this is the kind of platform G2 users keep shortlisting.
In the feedback I reviewed, the first throughline is performance consistency. G2 users frequently note that Cato’s global private backbone and dense PoP presence smooth out latency spikes and Internet variability, especially for SaaS and real-time traffic. The single, cloud-delivered console centralizes network and security policy, live traffic analytics, and incident views, which reviewers say reduces swivel-chairing and speeds troubleshooting. For many organizations, that combination turns day-two operations into a faster, more routine motion.
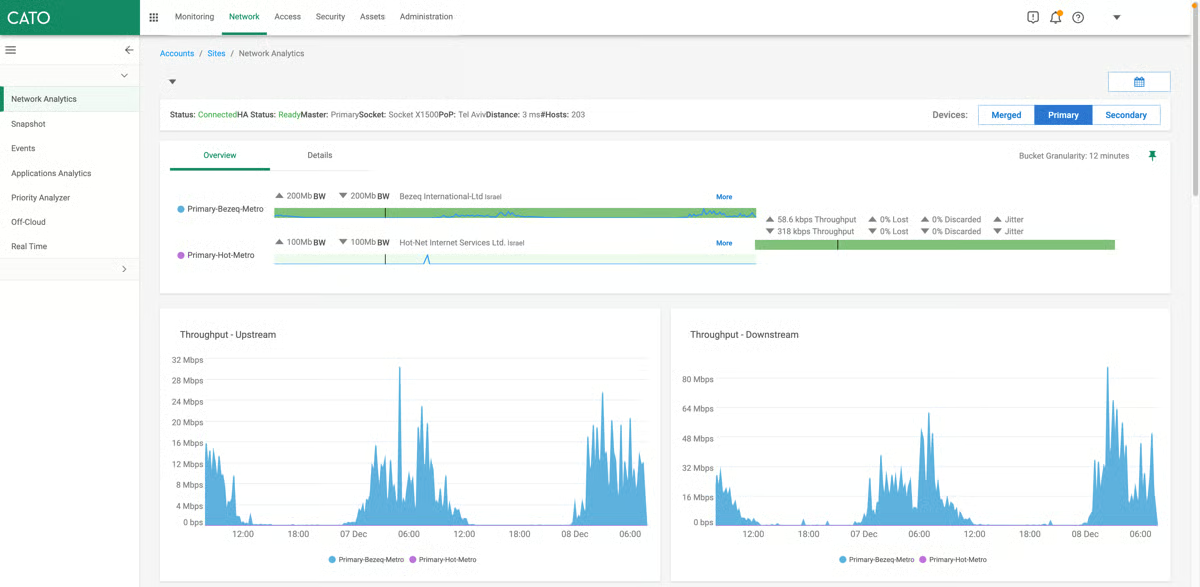
A second theme is convergence without contortions. G2 reviews consistently call out how SD-WAN and security controls live side by side: app-aware routing, QoS, and link remediation run alongside SWG/CASB, ZTNA, and firewalling, so you don’t have to daisy-chain vendors or hairpin traffic through a central hub. Admins highlight the practical effects: fewer VPN tickets, cleaner least-privilege access to private apps, and policy reuse across locations and users.
When it’s time to bring a new site online, reviewers say deployment is methodical and quick: ship an edge device, register it, attach policies, and you’re on the backbone with security controls already in line. 93% of G2 reviews rate the network segmentation highly, ensuring administrative control over network components, mapping, and segmentation.
G2 users also emphasize visibility and control. The platform’s real-time analytics and historical reporting make it straightforward to see who accessed what, from where, and under which policy, which helps both with incident timelines and with routine capacity planning.
Many reviewers point to MDR options and proactive support as force multipliers: when something drifts, you hear about it with actionable guidance rather than discovering it during an outage window. That support experience shows up often in comments about smoother rollouts and shorter time-to-value.
G2 reviewers appreciate the unified model, but teams coming from appliance-heavy networks often spend the first weeks mapping legacy rules to cloud policies and tuning ZTNA app definitions so prompts and paths reflect real usage. Reviewers frame this as an onboarding reality, not a blocker, and note that once policies settle, tickets drop and routing/security feel predictable.
Pricing scales with footprint. As you add regions, sites, and app coverage, total spend grows, so budgets need upfront modeling to avoid surprises, according to G2 budget owners. This model suits organizations pursuing global coverage and tool consolidation (SD-WAN + security + ZTNA in one service) who value paying in proportion to usage. However, it’s less ideal if you expect flat, set-and-forget pricing regardless of growth. Teams that model growth early say spend becomes predictable, consolidation trims vendor sprawl and support contracts, and the operational upside holds, fewer brittle tunnels, consistent inspection, and a single policy plane as the network expands.
G2 feedback describes steady payoff: branches and remote users ride the same backbone with consistent inspection, ZTNA replaces brittle tunnels, and admins operate from a single policy plane that travels with users and apps.
What I like about Cato SASE Cloud:
- The global private backbone + dense PoPs smooths real-world latency and makes SaaS/real-time traffic feel consistent.
- True convergence: SD-WAN lives alongside SWG/CASB, FWaaS, and ZTNA, so sites come online methodically (ship, register, attach policies) and you can reuse policies across users/locations.
What G2 users like about Cato SASE Cloud:
“What I like best about Cato SASE Cloud is the centralized, all-in-one platform that seamlessly combines SD‑WAN, firewall, SWG, CASB, and ZTNA services under a single pane of glass. Deployment and onboarding are fast—spinning up new sites takes under an hour — and day-to-day management is far simpler compared to juggling multiple tools, separate interfaces, and licenses.”
– Cato SASE Cloud review, Mohan S.
What I dislike about Cato SASE Cloud:
- Coming from an appliance-heavy past, you’ll likely map legacy rules to cloud policies and tune ZTNA app definitions in the first weeks; teams say this upfront work pays off as tickets drop and paths become predictable.
- Pricing is best modeled upfront, especially for many small sites or app-dense estates, but consolidation (backbone + SD-WAN + security stack) can offset the cost and simplify vendor sprawl.
What G2 users dislike about Cato SASE Cloud:
“What I dislike about Cato SASE Cloud is that advanced customization and granular control options are somewhat limited compared to traditional firewalls. Reporting and analytics could be more detailed and flexible, and policy updates sometimes take a few minutes to apply. While the platform is stable and improving, it’s still maturing in some enterprise-level features.”
– Cato SASE Cloud review, Faiz P.

Best zero trust networking software: Frequently asked questions (FAQs)
Got more questions? G2 has the answers!
Q1. What’s the best zero trust platform for cloud services?
For cloud-first access, pair Okta for identity-driven SSO/MFA and conditional access with Zscaler Private Access (ZPA) for user-to-app connectivity without VPNs. If offices/branches need consistent performance too, Cato SASE Cloud adds a global backbone with inline security so cloud apps stay fast and governed end to end.
Q2. What are the top zero trust network solutions for small business?
Lean teams typically get quick wins with ZPA (simple, policy-driven access to internal apps) anchored by Okta (easy SSO/MFA and app assignments). If you also want one console for connectivity + security as you grow, Cato SASE Cloud consolidates SD-WAN and security controls without appliance sprawl.
Q3. What are the best zero trust providers for enterprise cybersecurity?
Enterprises often combine Okta (directory/SSO/MFA + lifecycle) with Cato SASE Cloud (global SD-WAN + SWG/CASB/ZTNA). For plants, labs, or smart buildings, Palo Alto Networks IoT/OT Security adds device discovery, risk scoring, and segmentation.
Q4. What are some zero trust networking app recommendations?
For internal apps, ZPA brokers direct user-to-app access based on identity and device posture. Keep permissions clean in Okta (groups, conditional access), and harden endpoints with ThreatLocker (allowlisting + ringfencing) so approved apps can only do what they should.
Q5. Which zero trust product should we use for network safety?
If “network safety” means cutting lateral movement and stopping risky executables, ThreatLocker gives you a default-deny on endpoints, while ZPA removes broad network exposure by going app-by-app. Use Okta to centralize authentication so access stays tied to the user and device context.
Q6. What is the most reliable zero trust service for our tech startup?
Startups usually want fast rollout and minimal overhead: Okta for quick SSO/MFA and clean onboarding/offboarding, plus ZPA to publish internal tools without standing up VPNs. If you’re opening offices or need WAN + security in one place, Cato SASE Cloud keeps it simple as you scale.
Q7. What are the leading zero trust software for protecting business data?
Protect data by aligning identity, access, and endpoints: Okta applies conditional access, ZPA ensures least-privilege paths to sensitive apps, and ThreatLocker prevents unapproved binaries or scripts from touching protected files. For site-to-site traffic, Cato SASE Cloud enforces policy everywhere.
Q8. What is a trusted zero trust provider for SaaS companies?
SaaS-heavy teams do well with Okta (centralized SSO/MFA and app governance) plus ZPA (secure access to private build tools, admin panels, and databases). If you operate globally, Cato SASE Cloud adds a consistent security layer and performance baseline for SaaS and private apps alike.
Q9. What is a zero trust solution for securing an office network?
If offices/branches are in scope, Cato SASE Cloud converges SD-WAN and security (SWG/CASB/ZTNA) on a cloud backbone, so policy is consistent everywhere. Use Okta to gate access and ZPA to reach internal apps securely; for facilities with connected devices, add Palo Alto Networks IoT/OT Security to discover and segment IoT/OT.
Ready to retire your VPN?
Building durable access control shouldn’t mean wrestling with clunky clients or brittle network tunnels. The five tools I tested make it easier to deliver secure, personalized access, whether you’re focused on retiring VPNs, segmenting sensitive apps, or enabling contractors and BYOD safely.
Each pick is a highly recommended option for reducing the attack surface and stabilizing the user experience. Some shine for fast, lightweight rollouts; others go deeper with analytics and segmentation as you scale. I highlighted what each does well, and where to watch for limits, so you can move faster toward a zero trust posture that actually holds up.
Now it’s your turn: compare your top two or three, map them to your stack and risk areas, and choose the platform that keeps users moving while keeping threats contained.
Ready to layer adaptive challenges on top of ZTNA? Explore the best risk-based authentication software to pair zero trust access with step-up MFA based on user and device risk.


Leave A Comment